Exclusive VPN on Google Pixel phones and important details about ending VPN offer for everyone
As of now, anyone can use Google One VPN if they book the right subscription through Google One. But this...
How accessible are game engines and what work still needs to be done?
In some ways, game development is easier than ever. Between the availability of engines like RPG Maker and the release...
Samsung probably can’t get the camera problem under control
There are more new flagship smartphones in the market, from Honor, Huawei, Xiaomi and Co. Now added new models for...
Apple publishes open source AI models that run on devices
Apple today released several open source Large Language Models (LLMs) designed to run on devices rather than cloud servers. The...
They reveal which game Sonic 3 The Movie is inspired by
At this time, many new developments are coming about Sonic 3 the movieAs it has been mentioned that they have...
Who is Bastion in the X-Men 97 series?
By Aldo Lawson 0 comments 24/04/2024 7:16 pm series of X-Men 97 Gradually surprised the audience who enjoy its fantastic...
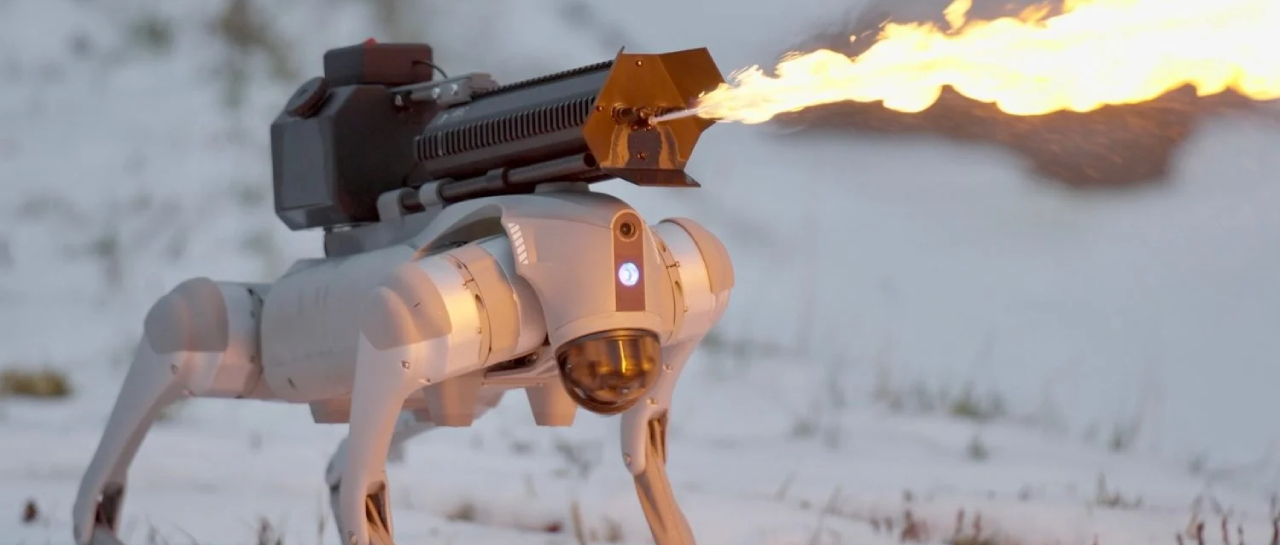
Includes robot dog with flamethrower
Although it may seem like something from a science fiction movie, robotics has developed, there are already fully functional models...
Microsoft to close Bethesda in France
As already established at the beginning of the year, Microsoft has some new plans that will recover the purchase investment...