What is DNS?
DNS (Domain Name System) is a service that converts hostnames to IP addresses. It is an application layer protocol that allows users and servers to exchange messages. Each host is identified by its IP address, but remembering numbers is extremely difficult for humans, and IP addresses are not static. As a result, DNS converts a site’s domain name to its numerical IP address.
What is DNS Tunnelling?
DNS tunneling uses the DNS protocol to tunnel malware and exfiltrate the data.
Attackers set up a server on which malware is running and a domain that points to it. Using a server that has been infected with malware, the attacker searches for the attacker-controlled domain. The DNS resolver creates a tunnel between the attacker and their target when it routes the query, allowing them to obtain data, remotely control the host, or otherwise carry out the attack.
Working on DNS tunneling attack chain
The image below shows step by step working of DNS tunneling.
Fig: 1
- The bad actor has a server running malware on it, with a domain pointing to that server.
- The attacker uses a host they have infected with malware to query for the attacker-controlled domain.
- When the DNS resolver routes the query, it creates a tunnel from the attacker to their target, allowing them to get data, remotely control the host, or otherwise take the next step in the attack chain.
DNS Tunneling Threats:
DNS tunneling is a mechanism that enables bad things to happen.
- Data Exfiltration: Threat actors use DNS to leak sensitive information. With all the extra overhead and encoding, it’s not the most efficient way to get information from a casualty’s PC, but it can work.
- Command and Control (C2): Hackers use the DNS protocol to send simple commands to a remote access trojan (RAT).
- IP-Over-DNS Tunneling: Some utilities have implemented the IP stack on the DNS query-response protocol. Using standard communications software like FTP, Netcat, and ssh would make data transfer relatively simple.
Common DNS Tunneling Toolkit:
DNSCat2: This toolkit is divided into two sections, client and server. The large server can maintain connections with many customers, making it an essential C&C worker. It should be the first to run ahead of any of the customers. Encryption, sessions like Metasploit, and tunnels for TCP forwarding are just a few features. However, we may encounter issues with the toolkit, such as slow performance, limited sessions, and tunneling limitations.
Once the DNScat2 installation is done, the server will run with the following command:

Fig: 2
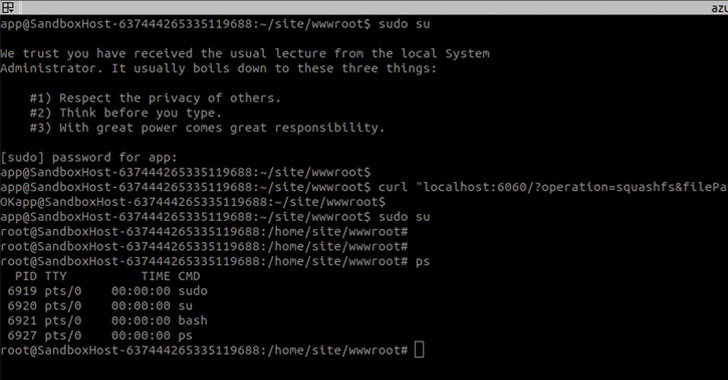
To establish a connection between client and server, use the following command on the client machine:

Fig: 3
One can also use Wireshark to verify that the session was successfully created. P ort 53 plays a significant role in gaining a reverse shell because security devices rarely block it, and in scenarios where a system hosts more than one NIC card, traffic from both cards travels through a single DNS.
The DNS protocol is based primarily on UDP. There’s no guarantee for the arrival of messages in the order they were sent. This is handled by DNS tunnelling tools by either enforcing TCP communication over the DNS or sending constant ping messages between requests to assure the correct order. Applying these methods for integrity increases the rate of messages over the DNS protocol. Also, when a DNS tunneling tool is used for either web browsing or file transfer, the volume and length of messages will increase compared to normal DNS traffic behavior.
Due to the latter, we expect the presence of DNS tunneling to cause a significant change in the DNS traffic with regards to (1) volume, (2) messages length, and (3) a shorter mean time between messages.

Fig: 4
Once the connection is established, you will see a session on the server, as shown in the image below. You can use the command ‘sessions’ to see if a new session has been created.

Fig: 5
We can now access the session and interact with many available options. This will create a new session two and to interact with it, and we will have a traditional shell.

Fig: 6
Detecting DNS Tunneling:
Payload analysis and traffic analysis are the two main methods for monitoring DNS and detecting attacks.
The contents of DNS requests and responses are examined in payload analysis. Suspicious activity can be detected using factors such as the size difference between the request and the response and unique hostnames.
To separate regular DNS traffic from malicious behavior, traffic analysis uses information such as the number of requests, geographic locations, and domain history. Network detection and response, for example, uses machine learning to establish a baseline for what normal DNS behavior looks like in any given environment, then sends out alerts when abnormal behavior occurs, which could indicate an attack.
How Quick Heal Technologies protect its customers:
HIPS module in QH identifies and blocks malicious activities like DNS tunneling based on network rules & data exfiltration to protect our customers.
Conclusion:
For all businesses, DNS is essential. Unfortunately, preventing DNS-based threats is a difficult task, and hackers are exploiting its inextricable but not entirely apparent exploitable surface. The techniques mentioned above will help detect and prevent DNS tunneling.