YouTube ad blocker is prohibited Atomics
It's no secret that advertising is a necessary ingredient for the survival of a platform like YouTube. However, the number...
Nintendo Confirms New Indie World | Atomics
As usually happens with Nintendo, the Japanese company unexpectedly revealed that there will be a new digital presentation in less...
Huawei is ending an era
In China, Huawei is closing in on Apple again and could become the smartphone market leader again in the long...
The CEO says the transmog system in Helldivers 2 is “just pointless.”
We suspect we were the ones wondering if some sort of transformation system might be available for fashion-conscious Helldivers 2...
Spotify plans to launch a lossless Music Pro subscription
A recent report suggests that Spotify is planning to raise its subscription prices soon, at least in some countries. And...
The former Blizzard boss thinks the game should have tips
For some time, video game prices have been established, ranging from $10 USD for some indies to $70 USD for...
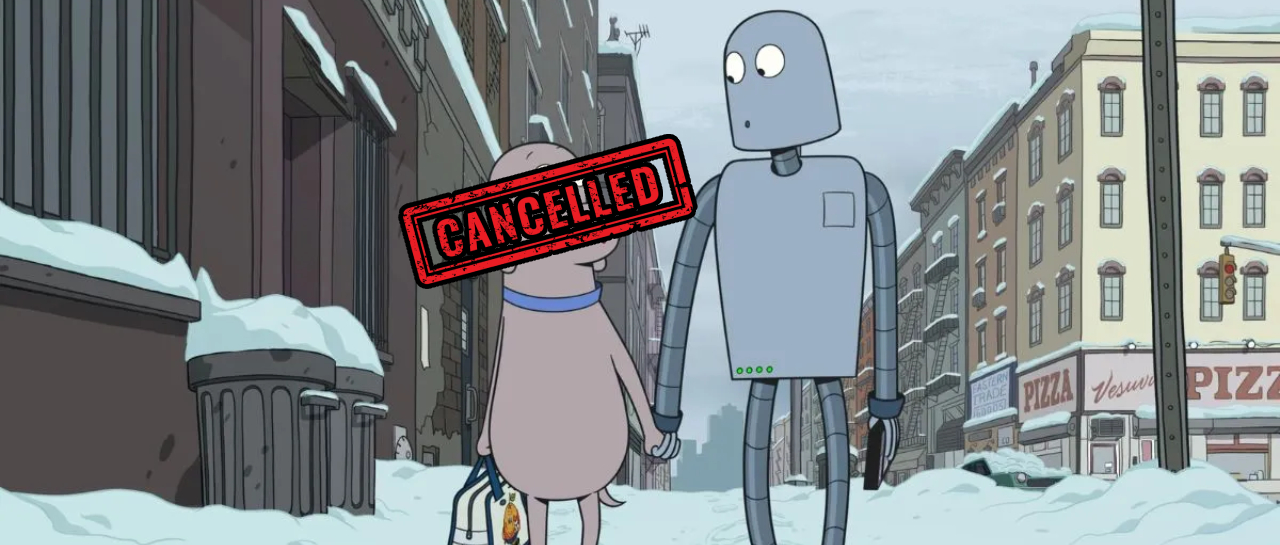
Social media is canceling the dog of robot dreams
This year there are some films which have become a sensation and which have undoubtedly grabbed the most attention Robot...
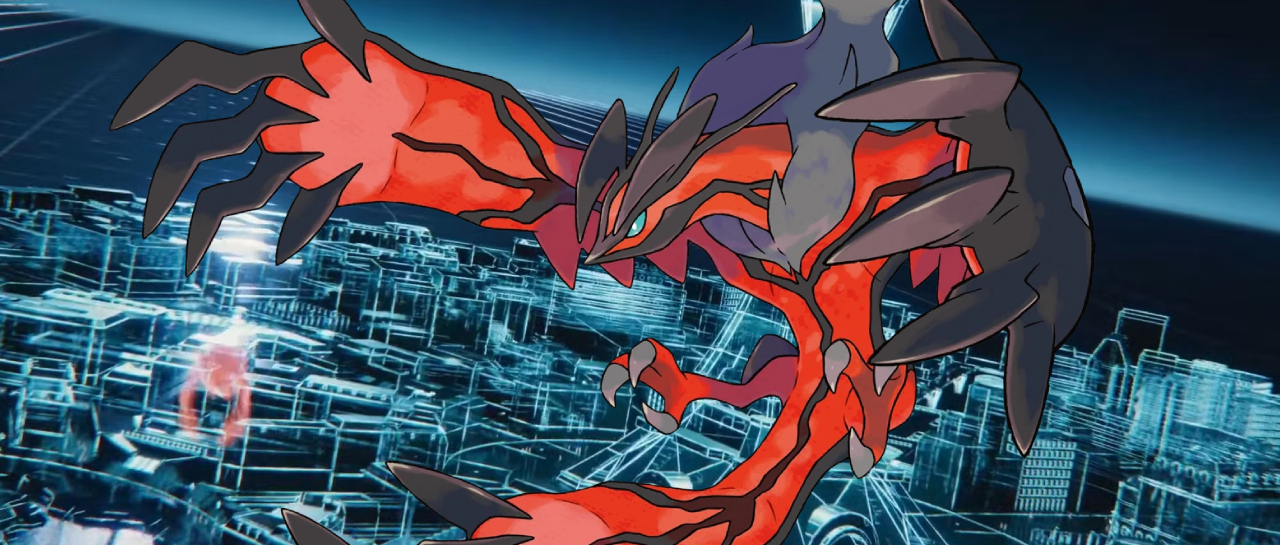
New details on Pokemon Legend: ZA
A few months ago we had a new live show from the well-known Pocket Monster JapanWhere we were introduced first...