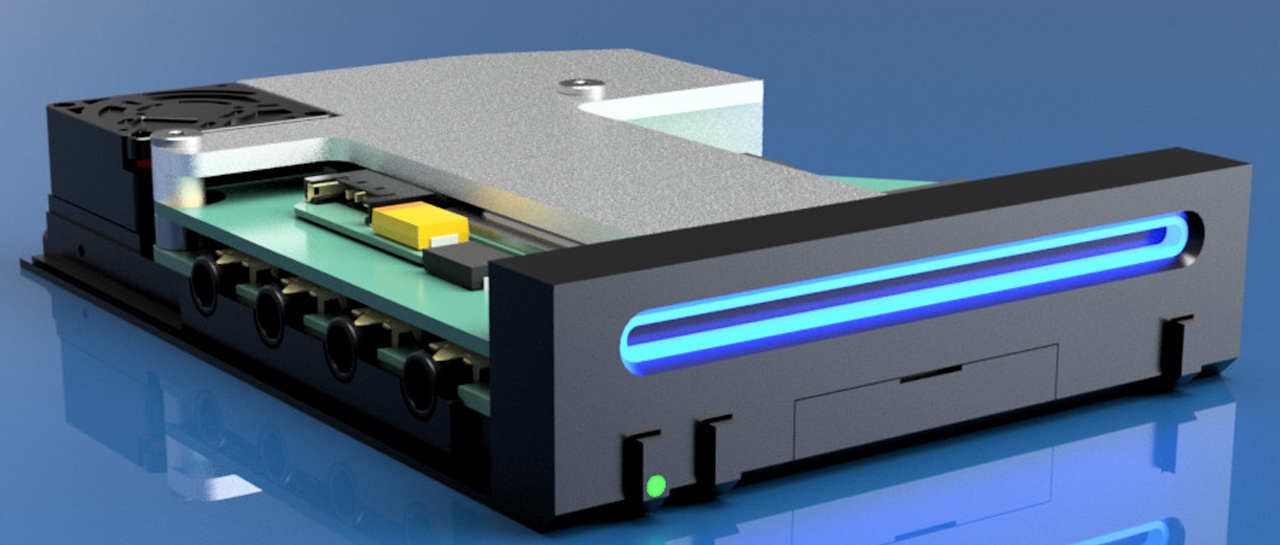
The Wii Mini is a reality, and it works Atomics
After the success of the NES and SNES Mini, many would think that Nintendo would offer smaller versions of its...
Samsung makes new hardware for Pixel 9 official
A few days ago, insiders announced that Google will also use the new Samsung hardware for the Pixel 9. What...
Nothing integrates ChatGPT into its in-ear headphones and NothingOS
Nothing just announced that it's going to integrate ChatGPT into its smartphone operating system, Nothing OS, and software for all...
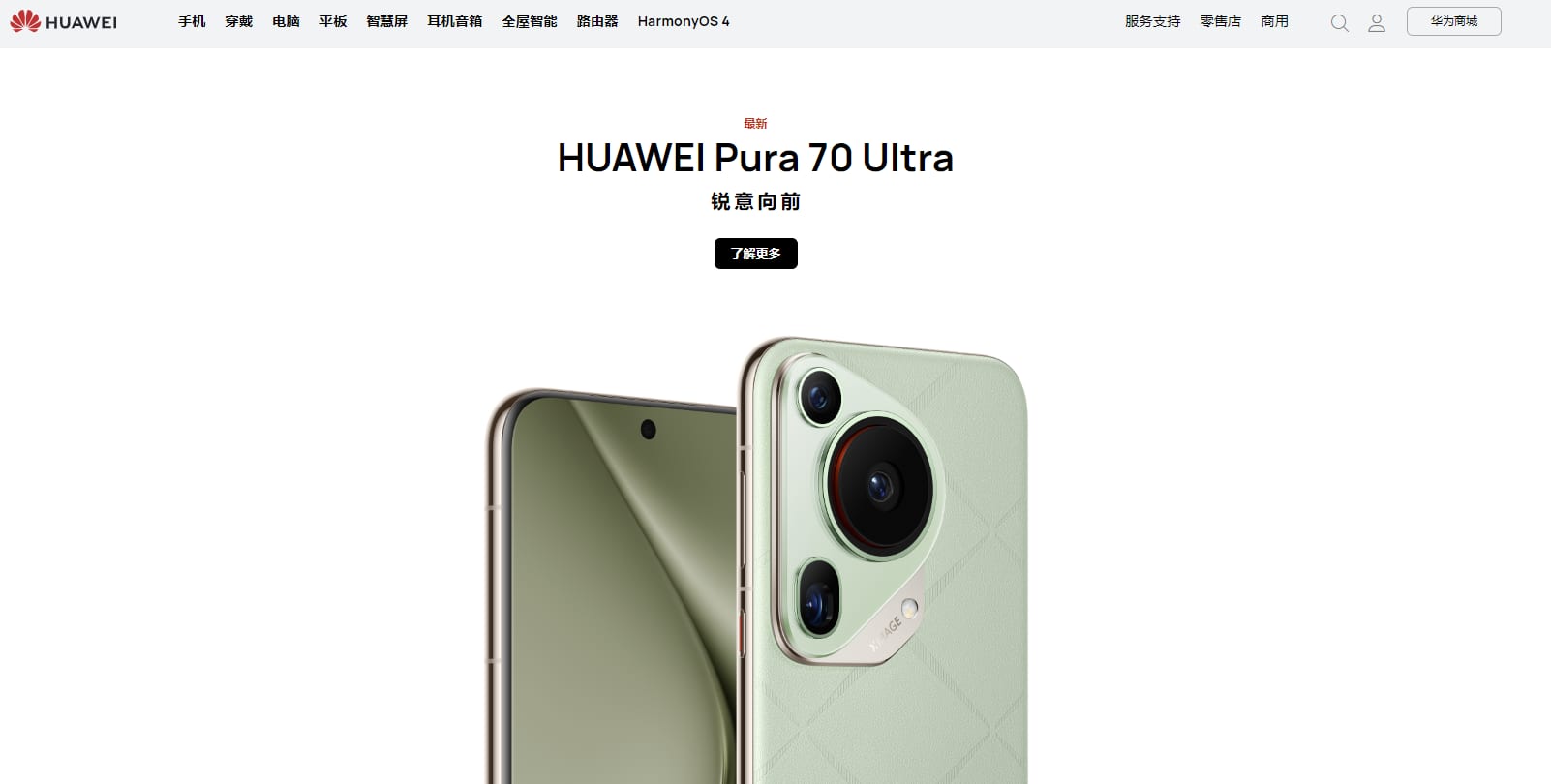
Huawei launches Pura 70 smartphone to challenge Apple in China
The bans, which began in 2019, nearly wiped out Huawei's smartphone business. Now Huawei is trying to come back. According...
Samsung is planning a feature for Galaxy phones that we’ve been waiting for years
In some ways, software from brands like Samsung and Xiaomi is significantly different from the original Android operating system. But...
A Manhattan high school student develops an amazingly accurate AI algorithm that predicts the resources needed for emergency calls.
Subway Exclusive pretend Steve Janowski published 17. April 2024 has been updated April 17, 2024 at 5:19 pm ET A...
The new Demon Slayer game was leaked
Leaks are the order of the day in the world of video games, as a new game in the franchise...
Assassin’s Creed Hex will be a horror game
There are many projects at the moment Assassin's Creed Plans to come in the coming years include us Codename Red,...