The United States has cyber security and intelligence agencies To warn About China-based state-sponsored cyber actors to exploit network vulnerabilities to exploit public and private sector entities from at least 2020 onwards.
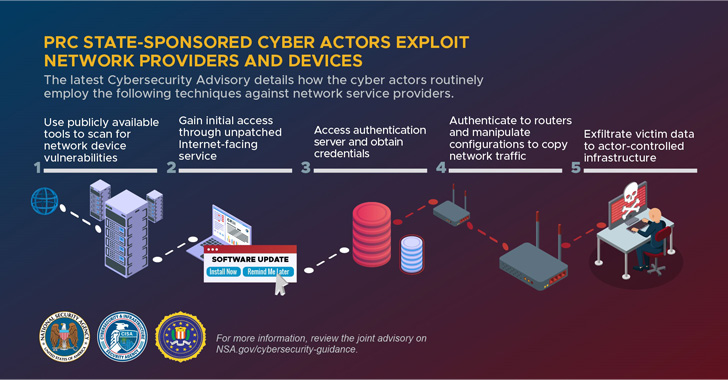
The goal of the broader penetration campaign is to exploit security vulnerabilities commonly identified on network devices such as small office / home office (SOHO) routers and network attached storage (NAS) devices aimed at gaining deeper access to victim networks.
In addition, the actors used these compromised devices as root command-and-control (C2) traffic to break other targets on the scale, in the US National Security Agency (NSA), Cybersecurity and Infrastructure Security (ISI), Says In a joint consultation.
Criminals are known to use a mix of open-source and custom tools for reconnaissance and vulnerability scanning to obscure and confuse their activities, in addition to changing their tactics in response to public disclosure.
Attacks are facilitated by accessing compromised servers from China-based IP addresses, which agencies call hop points, using them to host C2 domains, email accounts and communicate with target networks.
“Cyber actors use these hop points as a vague tactic when interacting with victim networks,” the agencies noted, describing the antitrust pattern of telecommunications companies and network service providers.

After stepping into the network through an unpatched Internet-oriented resource, actors were seen obtaining certificates for user and administrative accounts, then router commands were seen to “secretly route, capture and drive traffic outside the network to control the actor.”
Last but not least, the attackers also modified or removed local log files to further hide their presence and delete evidence of their activity to avoid identification.
The agencies did not identify any specific threat actors, but noted that the results reflected Chinese state-sponsored groups. History Of Aggressively aggressive Important infrastructure for stealing sensitive information, emerging key technologies, intellectual property and personally identifiable information.
The disclosure comes less than a month after the cyber security authorities Published The most commonly used primary access vectors for target breaches, some of which include incorrectly configured servers, weak password controls, unpatched software, and failure to block phishing attempts.
“Entities can reduce vulnerabilities listed in this consultation by applying available patches to their systems, replacing end-of-life infrastructure and implementing a centralized patch management program,” the companies said.