Cybersecurity researchers have unveiled a new ransomware strain Good luck Which forces victims to donate for social reasons and provides financial assistance to people in need.
“Ransomware group promotes very unusual demand for decryption keys,” said researchers at CloudSEK. Says In a report published last week. “The Robin Hood-like group claims to be interested in helping the less fortunate rather than extorting victims for financial incentives.”
Written on .NET, the ransomware was first identified by an India-based cybersecurity firm in March 2022, allowing sensitive files to be accessed without decryption. Malware, which uses AES algorithm For encryption, it is also significant to sleep for 722.45 seconds to interfere with dynamic analysis.
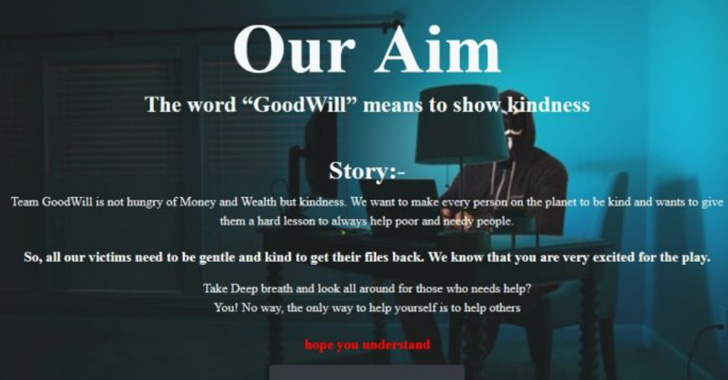
The encryption process is followed by displaying a multi-page ransom note for which the victim has to perform three socially driven activities in order to be able to get the decryption kit.

This includes donating new clothes and blankets to the homeless, taking any five underprivileged children to Domino’s Pizza, Pizza Hut or KFC for treatment and providing financial assistance to patients who need emergency treatment but cannot afford it. So
In addition, victims were asked to record activities in the form of screenshots and selfies and post them as evidence on their social media accounts.
“Once the three activities are over, the victims will also have to write a note on social media (Facebook or Instagram) about ‘How you transformed yourself into a kind person by being a victim of a ransomware called Goodwill,'” the researchers said.
Goodwill has no known victims and it is not yet clear if their exact tactics, tactics and methods (TTPs) have been used to facilitate the attack.
The identity of the threatening actor is also unknown, although an analysis of the email address and network artifacts reveals that the operators are from India and they speak Hindi.
Further investigation of the ransomware sample also revealed significant overlap with another Windows-based strain. Secret tearThe first ransomware to be open-source in 2015 as a proof-of-concept (PoC) by a Turkish programmer.
“Goodwill operators can gain access to it so they can create a new ransomware with the necessary modifications,” the researchers said.