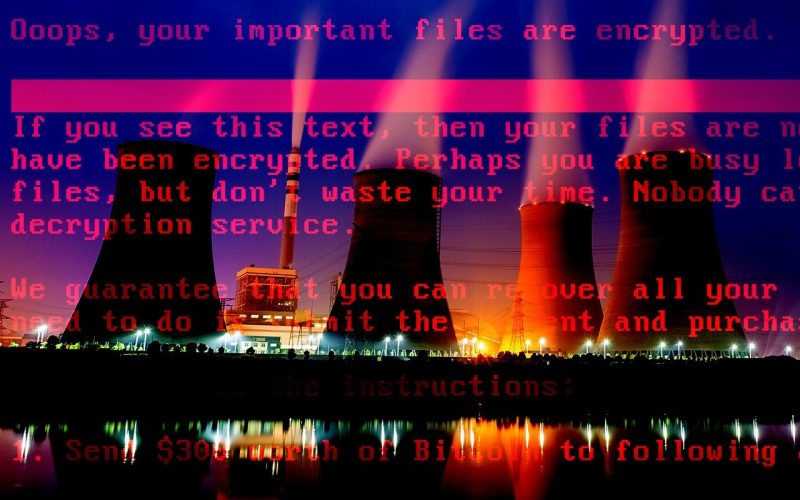
Threat actors have developed custom modules to compromise various ICS devices as well as Windows workstations that pose an imminent threat, particularly to energy providers. .
Source link
Feds: APTs Have Tools That Can Take Over Critical Infrastructure
0
Related Posts

Popular Stories
-
From Duskwood to Moonvale: Everbyte announces new interactive true crime game
-
Horizon Forbidden West, new major event: all accounts
-
OWC adds Thunderbolt 4 Dock, USB-C Dock and Storage Solutions | CineD
-
iPhone 12 mini Review | Trusted Reviews
-
The United States has revealed new and threatening nuclear weapons