A new malware tool that enables cybercriminals to create malicious Windows shortcuts (.LNK) The files have been viewed for sale on the Cyber Crime Forum.
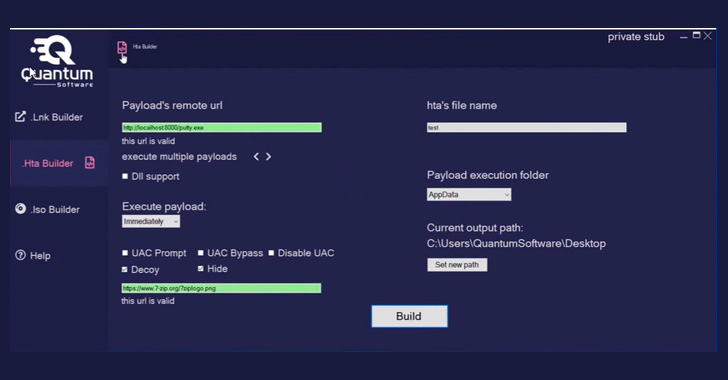
Dubbed Quantum LNK BuilderThe software makes it possible to bypass any extension and choose from over 300 icons, not to mention support UAC And Windows smart screen Bypass as well as “multiple payloads per .LNK” file. Also given the ability to create .HTA and disk image (.ISO) payloads.
Quantum Builder is available for lease at various price points: মাসে 189 per month, € 355 for two months, € 899 for six months, or এক 1,500 as a one-time lifetime purchase.
“.LNK files are shortcut files that specify other files, folders, or applications to open.” Says In a report “The [threat actor] Using LLNK files and dropping malicious payloads LOLBins [living-off-the-land binaries]”

Preliminary evidence of malware samples using Quantum Builder in the wild has been reported since May 24, disguised as innocent-looking text files (“test.txt.lnk”).
“By default, Windows hides the .LNK extension, so if a file is named file_name.txt.lnk, only the file_name.txt will be visible to the user even if the show file extension option is enabled,” the researchers said. “For this reason, it may be an interesting alternative to TA using .LNK files as camouflage or smokescreen.”

Launching the .LNK file involves executing PowerShell code, which runs an HTML application (“bdg.hta”) file hosted on Quantum’s website (“Quantum-Software”).[.]Online “) MSHTAA valid Windows utility used to run HTA files.
Quantum Builder will share the relationship with the North Korean-based Lazarus Group based on the tool’s source code-level overlap and the convenience of LNK files for next-stage payload delivery, indicating their potential use by APT actors. Attack
The development comes after Bumblebee and Emotet’s rear operators moved to .LNK files to trigger the transition chains after Microsoft’s decision to disable Visual Basic for Applications (VBA) macros by default earlier this year.
Bumblebee, a replacement for the marketloader malware that first appeared in March, serves as a backdoor designed to give attackers continued access to compromised systems and a downloader for other malware, including Cobalt Strike and Sliver.
The capabilities of malware make it a tool of choice for threatening actors. According to Sybil, 413 cases of bumblebee infection were reported in May 2022, up from 41 in April.
“Bumblebee is a new and highly sophisticated malware loader that uses a wide range of fraudulent techniques and anti-analysis techniques, including complex anti-virtualization techniques,” the researchers said. Says. “It could become a popular tool for ransomware groups to deliver their payloads.”